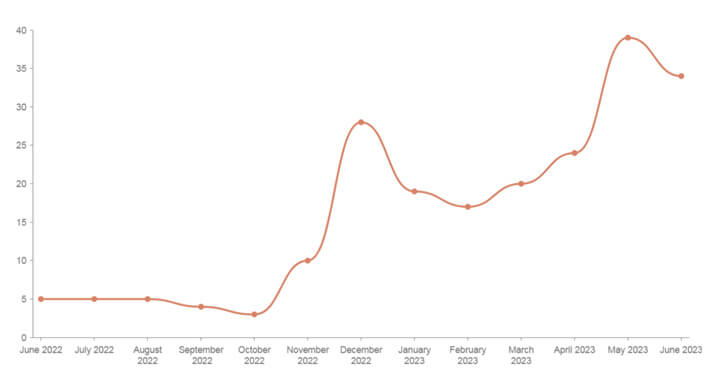
The Mallox ransomware group, also known as TargetCompany, Fargo, and Tohnichi, has become increasingly active, signaling significant changes to its operations. According to recent findings, Mallox ransomware activity in 2023 increased by a whopping 174% compared to the previous year.
researcher’s discovery
Security Researcher at Palo Alto Networks Unit 42, Declaration Like other ransomware criminals, Mallox employs a double extortion tactic. They steal sensitive data from compromised organizations before encrypting files, then leak the stolen data to exfiltrate sites to force victims to pay a ransom.
This ransomware group is associated with a wide range of threat actors associated with different ransomware variants, including TargetCompany, Tohnichi, Fargo, and Xollam.
characteristics
One of Mallox’s notable features is its way of exploiting insecure MS-SQL servers through dictionary attacks. These vulnerable servers act as an infiltration vector to infiltrate the victim’s network. However, researchers observed that Mallox deviated from this norm by using malicious OneNote attachments for initial access.
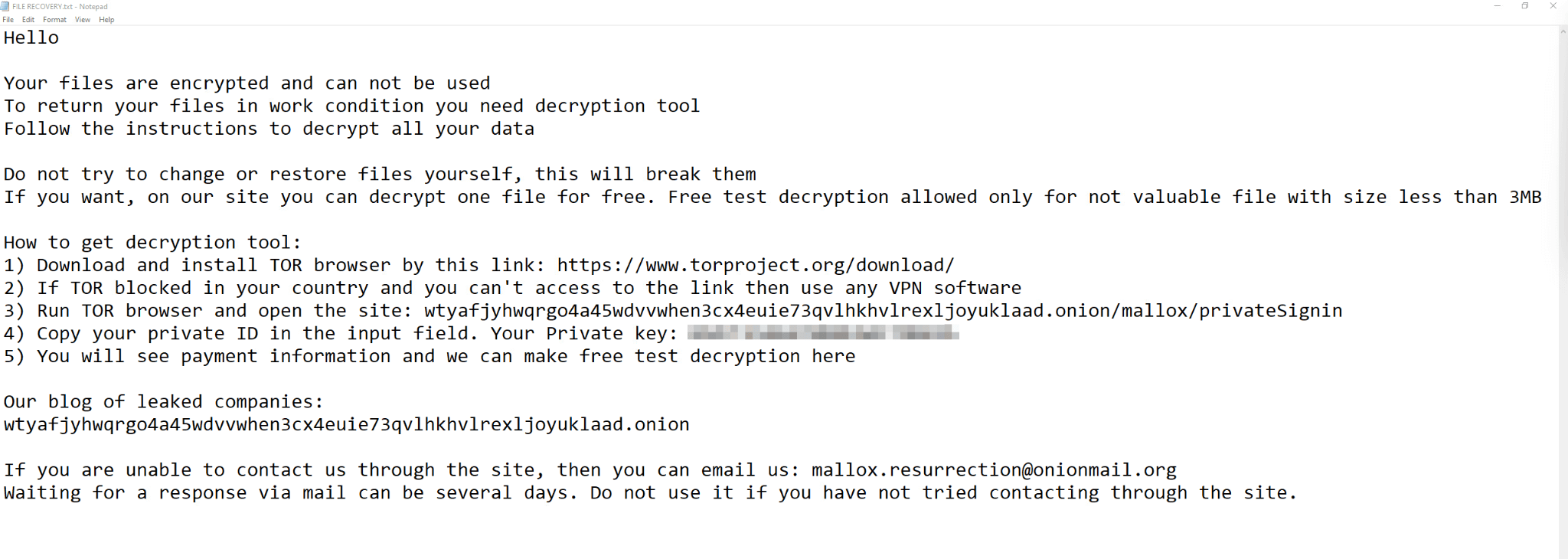
Additionally, once Mallox gains a foothold on the compromised host, it runs PowerShell commands to retrieve the ransomware payload from the remote server. The binary then takes action to disrupt recovery efforts by stopping and removing SQL-related services, deleting volume shadow copies, clearing system event logs, and terminating security-related processes. After encrypting the victim’s data, Mallox drops ransom notes in all directories.
Despite being a relatively small and closed group in the past, Mallox is actively recruiting affiliates for its Ransomware-as-a-Service (RaaS) program, which can be interpreted as a recent surge in activity.
Additional context and mitigation
The sudden increase in Mallox infections is part of a broader trend in the ransomware landscape. In general, ransomware attacks jumped 221% year-over-year as of June 2023, with a total of 434 attacks reported in June 2023 alone, largely attributed to the Clop ransomware group’s exploitation of a vulnerability in their MOVEit file transfer software.
Researchers have warned that the Mallox ransomware group’s increased activity and recruitment efforts could lead to more attacks on the organization if successful.
To defend against these threats, organizations are advised to ensure proper configuration of internet-facing applications, keep all systems patched and up-to-date, and implement endpoint security controls to detect suspicious activity. Proactive cybersecurity measures are the best defense against ransomware threats like Mallox.
You can find a full, comprehensive article at How to mitigate ransomwarehere.
If you like this article, follow us. LinkedIn, Twitter, Facebookand youtube Check out more cybersecurity news and topics.
