Estimated Reading Time: three minute
WordPress is a popular content management system that allows users to create and manage websites with the help of various plugins. One of the popular plugins used by over 60,000 websites is “WordPress Online Booking and Reservation Plugin – Bookly”. Bookly simplifies online booking and automates the booking process. However, like many other WordPress plugins, it can be vulnerable to exploitation by attackers.
In March 2023, Quick Heal Security Labs identified a vulnerability in the Bookly plugin. As soon as we discovered a flaw, we initiated a responsible disclosure process so that the vulnerability could be quickly addressed. On March 3, 2023, we contacted the Bookly plugin support team with full technical details after discovering the vulnerability earlier that day. We also reported the vulnerability to plugins@wordpress.org and Wordfence (CNA). This vulnerability was quickly identified and assigned the identifier CVE-2023-1172. The Bookly team developed a patch and released it as version 21.5.1 on March 9, 2023.
In this post, we will conduct a thorough analysis of the root cause of the vulnerability found in the Bookly plugin and a scan of the released patch to address the issue.
CVE analysis–2023-1172 – Unauthenticated saved cross-site scripting via name:
Our research has shown that the Bookly plugin’s “full name” field is vulnerable to stored XSS (cross-site scripting) attacks due to improper input sanitization and output escaping. Upon further investigation, we found that the plugin reuses the user’s “full name” input across multiple files, greatly increasing the risk of a security breach if the input is not properly sanitized and escaped to prevent malicious code injection. The code snippet below shows how the value of the “Full Name” field is utilized.
As shown below, the value of the “full name” field is stored in the variable $codes.
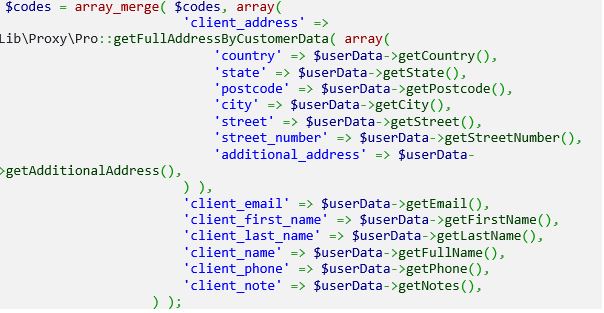
After that, the variable $codes is used in the calendar’s tooltip.
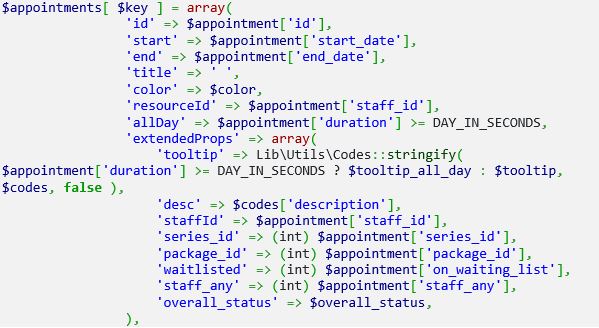
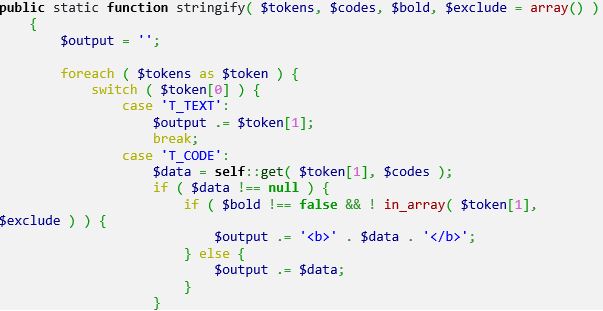
However, it appears to lack a proper sanitization action when using the $codes variable later in the program.
Troubleshooting: Looking at Patches
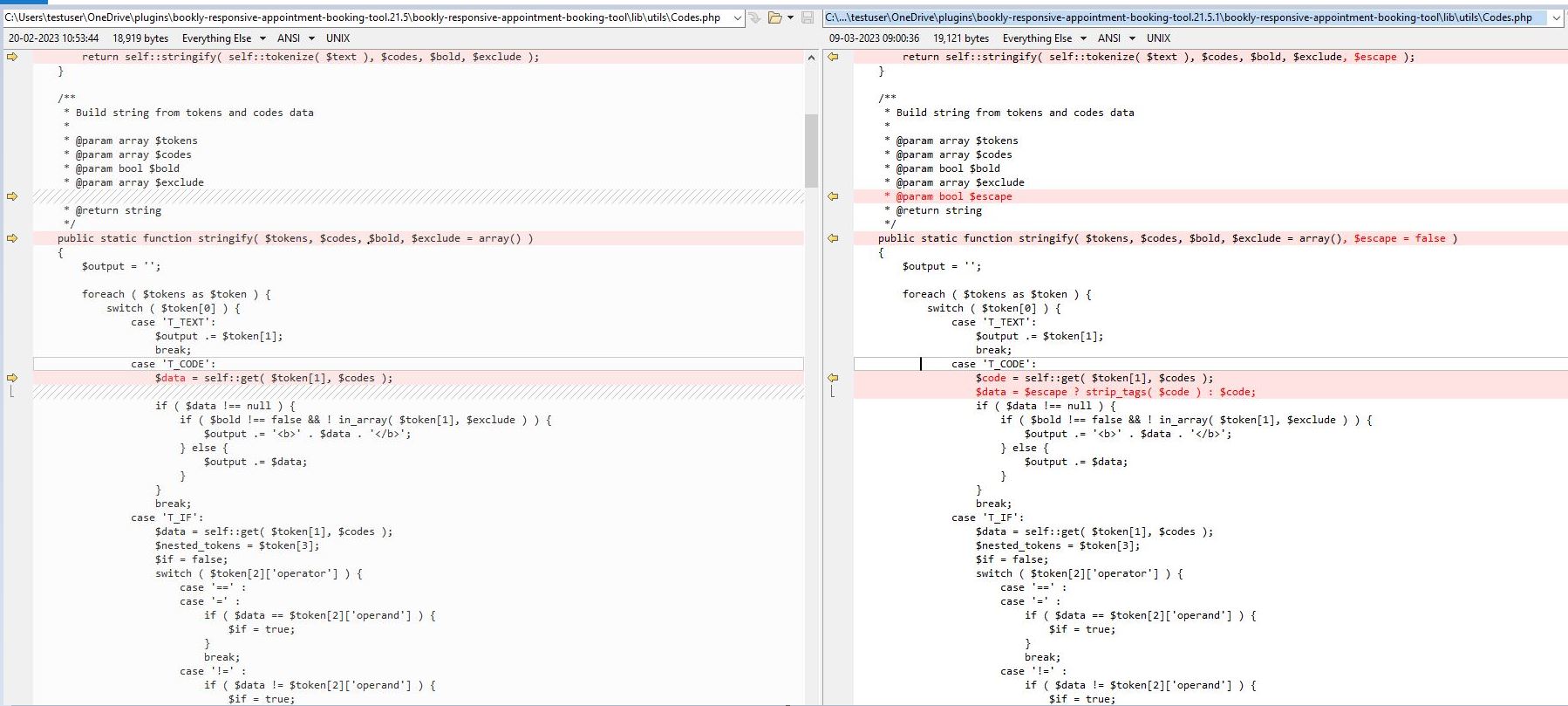
After investigating the patch that addresses the vulnerability, we discovered that the $codes variable was properly sanitized to prevent potential security breaches in the program. Specifically, this patch uses PHP’s “strip_tags” feature to sanitize the $codes variable and mitigate the attack before it’s used elsewhere in the code.
conclusion
This post highlighted a vulnerability in the Bookly plugin that could allow an unauthenticated attacker to inject a malicious script to compromise a site owner’s entire site when the plugin accesses the calendar tooltip. Thankfully, this vulnerability has been fully addressed in version 21.5.1. WordPress site owners are strongly encouraged to update their sites with the latest patched version of the plugin (current version 21.6) to prevent potential attacks.
All SEQRITE and Quick Heal customers are protected from exploits targeting this vulnerability with the following signature:
- HTTP/CVE-2023-1172!VK.46842
- HTTP/CVE-2023-1172!VK.47543
